Which of the Following Best Describes a Firewall
Data must be stored on a secure medium and special security measures must be enforced to protect such data on storage media and during transmittal. It checks only the IP and protocol.
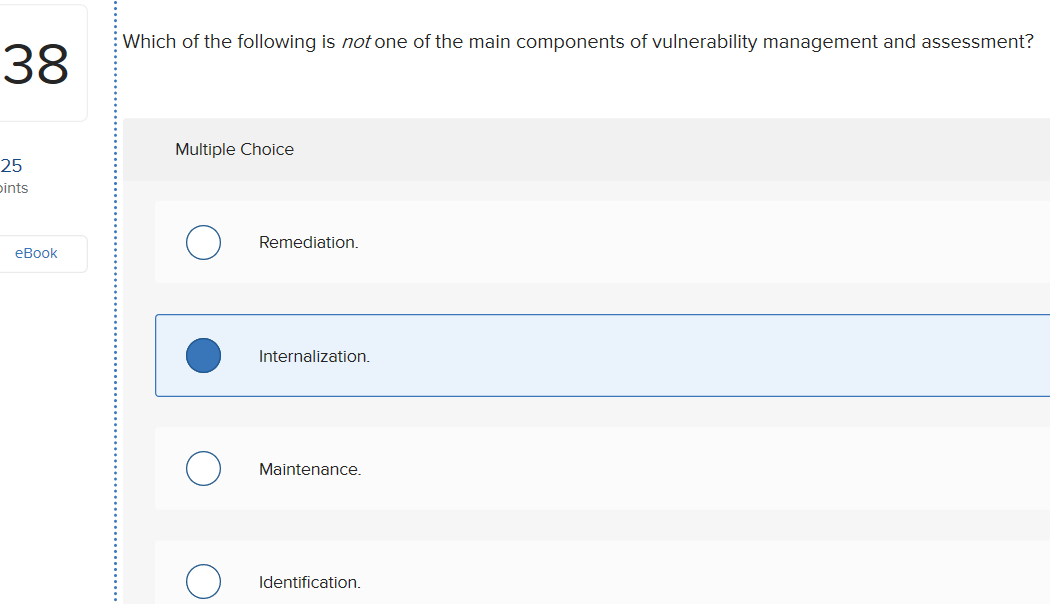
Solved Which Of The Following Best Describes What Is Meant Chegg Com
You are asked to configure your firewall in such a way that the traffic from source address range 1171121025 through 11711215100 is allowed while traffic from 1171121225 through 1171121325 is denied and traffic from 11711212200 through 1171121310 is.

. B This is the zone outside the proprietary network. Which of the following best describes a firewall. It sends traffic through another host.
Which of the following statements best describes a stateful packet inspection firewall. 4 rows Which of the following best describes a host-based firewall. B A tool that searches Web pages containing the users search terms and then displays pages that match.
A proper email address is a combination of the email prefix and email domain both in appropriate formats. Which of the following BEST describes a firewall. A device that analyzes traffic based on destination address c.
A a software and hardware system that prevents outsiders from accessing a companysinternal network B a tool that searches Web pages containing the users search terms and then displays pages that match C a private network of internal websites and other sources of information available to acompanys employees D an. Which of the following best describes a proxy firewall. Software firewalls are generally used to protect individual hosts.
Which of the following BEST describes a firewall. A firewall is a pass - through device that allows only certain traffic in and out. Hardware firewalls are physical devices that are usually placed at the junction or gateway between two networks generally a private network and a public network like the internet.
A load balancing system that acts as a funnel point for traffic that is an ideal place to enforce policy and that is done through the firewall d. AIt sends traffic through another host. 12 Which one of the following is a valid email address.
A firewall is designed to protect the computer from viruses and malware etc. It is typically run on the host system. C It works by examining the client application to determine if traffic is permitted.
Which Of The Following Best Describes A Firewall Is Quizlet. A A software and hardware system that prevents outsiders from accessing a companys internal network. A It examines each packet against a set of criteria.
It acts as a gateway for requests arriving from the client. Which of the following best describes the Gramm-Leach-Bliley Act. Which of the following best describes the cloud access security broker.
DIt is typically run on the host system. A firewall is a software or a hardware device that can filter incoming or outgoing traffic based on certain criteria. A host-based firewall is a.
Question 6 of 15 Which of the following best describes a proxy firewall. The domain appears to the right side of. The best simple firewall.
A firewall is a network segment off the firewall in which you put systems that require different levels of access than other network components. C This is a zone within the proprietary network that needs access from outside the proprietary network. A proxy installed between a firewall and a web server b.
A device that monitors the characteristics of a single host and the events occurring on that host. The current packet but also on data derived from previous packets in the conversation. A This is the zone inside the proprietary network.
CIt checks only the IP and protocol. A firewall is a pass-through device that allows only certain traffic in and out. It is typically run on the host system.
A A software and hardware system that prevents outsiders from accessing a companys internal network. The Gramm-Leach-Bliley Act requires financial institutions to ensure the security and confidentiality of customer data. BIt acts as a gateway for requests arriving from the client.
If we are forcing to make choices. Question 7 of 15. Which of the following best describes the concept of a DMZ when using firewalls.
Which of the following best describes a network chokepoint. A softwarehardware technology used to protect a network from outside attacks Which of the following types of firewall causes the largest reduction in the performance of the device on which it is instilled. Hardware firewalls can be a standalone product or can also be built into devices like broadband routers.
The following describes how firewalls are usually used.

Which Best Describes A Human Firewall
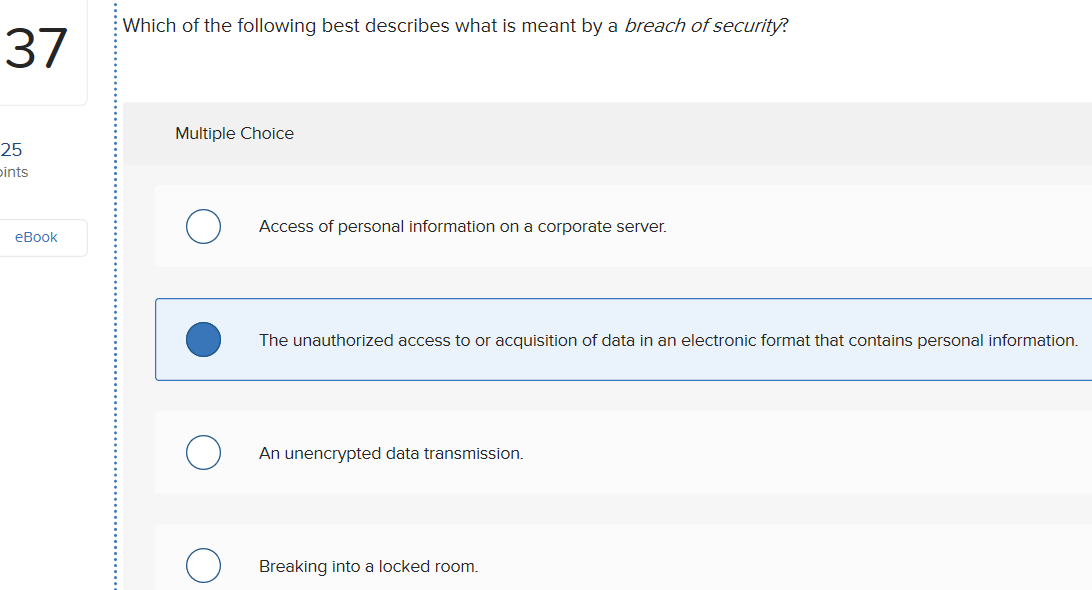
Solved Which Of The Following Best Describes What Is Meant Chegg Com

Vendor Comptia Exam Code N Ppt Download

Solved 29 Which Of The Following Best Describes East West Chegg Com
Comments
Post a Comment